Pseudorandom Number Generation and Stream Cipher
1. The Use of Random Number
1.1 Key Distribution : Two parties communicating by exchanging keys. In many cases nonces are used for handshaking to prevent replay attacks.
1.2 Session Key Generation : Sometime a short key is needed during short period of time such as bank transactions.
2. How to check Randomness
There are two ways to check randomness
2.1 Uniform Distribution : The frequency of occurrences of one and zero should be approximately equal.
2.2 Independence : No one subsequence in the sequence can be inferred from the other.
3. How to Evaluate Random Number :
3.1 The function should be full period generating function. That is, the function should generate all the numbers from 0 through m-1 before repeating.
3.2 The generated sequence should appear random.
3.3 The function should implement efficiently with 32 bit arithmetic.
4. True Random Number Generation (TRNG) :
It takes an Input as source which is effectively random source or entropy source. This source may be the processing time, keystroke time, mouse moments and some environment dependable resources.
4.1 When to Use TRNG : Dealing with small bit's of number perform good whereas using large number of bit become tedious.
5. Pseudo Random Number Generator(PRNG) :
In case of PRNG input is fix called as seed. It produces the output bit using the deterministic algorithm. Afterwards, for more complex output of algorithm is taken and fed as input to the algo to produce more bits or sequence of bits.
NOTE 1: If a person knows the seed value as well as algorithm then it is quite easy to generate the entire bit stream. 😒
6. Pseudo Random Function (PRF) :
It is used to produced a Pseudorandom string of bits of some fixed length.
Input = Seed + Context Specific Values.
NOTE 2: What is Context Specific Values 😄 : User ID, Application ID, etc.
7. PRNG Requirement :
Basically the requirement for a PRNG is that the generated bit stream appear random even though it is deterministic.
Actually, there is no way to check bit stream is random or not but we apply some multiple test and on the behalf of multiple test we check the system satisfies the randomness requirement or not.
Some test are :
7.1 Uniformity : number of one's and zero's should be equal.
7.2 Scalability : if a test applicable on a sequence then it should also be applicable on subsequence.
7.3 Consistency
7.4 Run Test or Frequency Test : How many time the random bit is generated and count the number of one's and zero's in every time.
7.5 Mourer's Universal Statistical Test : The focus of this test is the number of bits between matching pattern. The purpose of the test is to detect whether or not the sequence can be significantly compressed without loss of information. A significantly compressible sequence is considered to be non random.
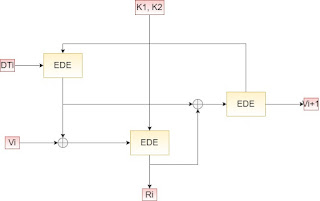
8. How to Generate Seed :
Figure 4 explains the generation of seed. The seed should be unpredictable or should be secure because if the seed is known to third person then it is quite very simple to break the message. so seed should be random or pseudo random.
NOTE 3: Why PRNG is used when TRNG is already present ??👀 The reason behind is that when the stream cipher is present then TRNG is not practical.
9. Pseudo Random Number Generators
9.1 Linear Congruential Generators :
This algorithm is parameterized with four numbers as follows:
m ---> modulus, m>o
a ---> multiplier, 0<a<m
c ---> increment, 0<=c<m
Xo --> seed/starting value, 0<=Xo<m
So sequence of number {Xn}is obtained via the following iterative equation
Xn+1 = (aXn + c) mod m
Here m, a, c, Xo are integers.
The selection of values for a, c, and m is critical in order to generate the random number.
NOTE 4: 1. A common criterion is that m be nearly equal to the maximum representable non negative integer. Thus, a value of m near to or equal to 2^31 typically chosen.
2. Since more than 2 billion possible choices for 'a', only a handful of multipliers pass all 3 tests. one such value of a = 7^5, which was originally selected for use in the IBM 360 family of computers.
So, if the opponent knows that the linear congruential algorithm is being used and if the parameter are known (e.g. a = 7^5, c=0, m = 2^31 - 1), then once a single number is discovered, all subsequent numbers are known.
9.2 Blum Blum Shub Generator :
First chose two large prime numbers Say P and Q and n = P.Q . Next, chose a random numbers, such that S is relatively prime to n; this is equivalent to saying that neither P nor Q is a factor of S.
The BBS Generator produces a sequence of bits Bi according to following algorithm .
|
|
PRNG |
TRNG |
|
Efficiency |
Very Efficient |
Generally Inefficient |
|
Determinism |
Deterministic |
Non Deterministic |
|
Periodicity |
Periodic |
Aperiodic |
|
k-Array |
---à |
3 |
1 |
4 |
1 |
5 |
3 |
1 |
4 |
|
i |
J |
S0 | S1 | S2 | S3 | S4 | S5 | S6 | S7 |
|
|
0 |
0 |
1 |
2 |
3 |
4 |
5 |
6 |
7 |
|
0 |
3 |
3 |
1 |
2 |
0 |
4 |
5 |
6 |
7 |
|
1 |
5 |
3 |
5 |
2 |
0 |
4 |
1 |
6 |
7 |
|
2 |
3 |
3 |
5 |
0 |
2 |
4 |
1 |
6 |
7 |
|
3 |
6 |
3 |
5 |
0 |
6 |
4 |
1 |
2 |
7 |
|
4 |
7 |
3 |
5 |
0 |
6 |
7 |
1 |
2 |
4 |
|
5 |
3 |
3 |
5 |
0 |
1 |
7 |
6 |
2 |
4 |
|
6 |
6 |
3 |
5 |
0 |
1 |
7 |
6 |
2 |
4 |
|
7 |
6 |
3 |
5 |
0 |
1 |
7 |
6 |
4 |
2 |
|
i |
J |
t |
Ks |
S0 |
S1 |
S2 |
S3 |
S4 |
S5 |
S6 |
S7 |
|
0 |
0 |
|
|
3 |
5 |
0 |
1 |
7 |
6 |
4 |
2 |
|
1 |
5 |
3 |
1 |
3 |
6 |
0 |
1 |
7 |
5 |
4 |
2 |
|
2 |
5 |
5 |
0 |
3 |
6 |
5 |
1 |
7 |
0 |
4 |
2 |
|
3 |
6 |
5 |
0 |
3 |
6 |
5 |
4 |
7 |
0 |
1 |
2 |
|
4 |
5 |
7 |
2 |
3 |
6 |
5 |
4 |
0 |
7 |
1 |
2 |











Comments
Post a Comment