Advance Encryption Standards (AES)
AES is a symmetric block cipher which converts Plaintext into Ciphertext.
AES can be AES-128, AES-192, AES-256 it depends on the length of key. The key length can be 16, 24, or 32 bytes. Fig. 1 explains the working of AES-128.
NOTE 1: if the key length is not in the form of 16, 24, or 32 bytes then we add some bits which is also called as padding.
Fig. 1: AES-128
Number of Rounds Number of Rounds (NR) always depends on number of bits in key.
NR = ( key Size / Block Size) + 6
NOTE 2: Here Block Size is always considered as 32 bit. This 32 and 6 is used because they offered the optimal trade off between security and performance. When you plot this point into continous function then you can do interpolation.
State Array
It stores the intermediate result after each step (As shown in Fig. 2). It is a 4 x 4 matrix in which a hexadecimal value is stored. The first four bit represents the row and last four bits represents the column value and these row and column value serves as indexes into the S-box to select a unique 8-bit value (as shown in Fig. 3).
Fig. 2: State Array after Every Step
Fig. 3: State Matrix
AES Transformation Function
1. Substitute Byte Transformation
In case of AES substitution mechanism is quite different from DES because substitution is done for each byte.
Only one table is used for transformation of bytes means if 2 bytes are same, the transformation is also same.
NOTE 3: At encryption side we interpret the bytes as 2 hexadecimal digits.
1st Hexadecimal digit ----> Row
2nd Hexadecimal digit ----> Column
Transformation is done one byte at a time. Fig. 4: Substitute Bye transformation
Now suppose we pick S(1,1) means first row first column, first four bits represents the row and rest last bits represents for column. It will pick the value and check it on the S-box and prints the value (as shown in Fig. 4).
Fig. 5: S-Box
How to Calculate the Value of S-Box ??😅
Suppose we want to calculate the value of {95} the first we will calculate the inverse of {95} using GF(2^8) (as shown in Table 1).
Table 1 calculate the value of {95} or {100101010}
|
q
|
r1
|
r2
|
r
|
t1
|
t2
|
t
|
|
10
|
100011011
|
1001011
|
110000
|
0
|
1
|
10
|
|
111
|
1001011
|
110000
|
10
|
1
|
10
|
1111
|
|
11000
|
110000
|
10
|
1
|
10
|
1111
|
10001010
|
|
10
|
10
|
1
|
0
|
1111
|
10001010
|
|
|
|
1
|
0
|
|
10001010
|
|
|
so the achieve output is {8A} or {10001010}.
Consider that each byte in the S-box consists of 8 bits labeled (b7, b6, b5, b4, b3, b2, b1, b0). Apply the following transformation to each bit of each byte in the S-box:
where ci
is the ith bit of byte c with the value {63}; that is, (c7c6c5c4c3c2c1c0) = (01100011).
The prime (') indicates that the variable is to be updated by the value on the right. The AES
standard depicts this transformation in matrix form as follows:
Hence the Value of {95} is {2A}
Fig. 6 shows the mapped value through S-Box.
Fig. 6: SubBytes Transformation
2. Shift Rows Transformation: This will shifts the row with different level of Rotations (as shown in Fig. 7).
Fig. 7: Shift Rows
3. Mix Columns Transformation:
In mix columns we multiply the previous state output with constant matrix.
Fig. 8: Multiplication With Constant Matrix.
NOTE 4: A.
Constant Matrix ?? 😅 : Constant matrix can be easily calculated by multiplied with specially crafted polynomial and take remainder after dividing by x^4+1.
Constant Matrix = (crafted matrix ).(polynomial of degree 3) % (x^4+1)
Constant Matrix = ((03a)x^3+(01b)x^2+(01c)x+(02d)).(ax^3+bx^2+cx+d) % (x^4+1)
= {2,1,1,3}
B. Crafted Matrix ?? 😒
For calculation of crafted matrix you need to first understand the Maximum Distance Separable (MDS) matrix. With the little bit knowledge of Codding theory and MDS matrix the crafted polynomial can be easily calculated.
C. Why Mix Column is not present at last Round?? 😐 At last level mix column doesn't increase the security moreover it slow down the things.
Since it is a multiplication with a constant matrix. Basically in actual is is a linear operation. Hence, adds no value and mix columns takes some time because it overheads some incurs in terms of software and hardware aspect but didn't give security.
4. ADD Round Key
the 128 bits of State are
bitwise XORed with the 128 bits of the round key (as shown in Fig. 9).
Fig. 9: ADD Round Key Mechanism
Key Expansion Algorithm
AES key expansion algorithm takes as input a four word (16- byte) key and produces a linear array of 44 words. This is sufficient to provide a four-word round key for the initial AddRoundKey stage and each of the 10 rounds of the cipher.
Fig. 10: AES Key Expansion
1 RotWord performs a one-byte circular left shift on a word. This means that an input word [B0, B1, B2, B3] is transformed into [B1, B2, B3, B0].
2. SubWord performs a byte substitution on each byte of its input word, using the S-box .
3. The result of steps 1 and 2 is XORed with a round constant, Rcon[j].
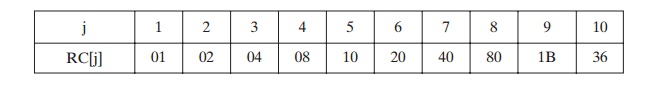
The round constant is a word in which the three rightmost bytes are always 0. Thus, the effect of an XOR of a word with Rcon is to only perform an XOR on the left- most byte of the word. The round constant is different for each round and is defined as Rcon[j] = (RC[j], 0, 0, 0), with RC[1] = 1, RC[j] = 2 RC[j -1] and with multiplication defined over the field GF(28). The values of RC[j] in hexadecimal are
For example, suppose that the round key for round 8 is
EA D2 73 21 B5 8D BA D2 31 2B F5 60 7F 8D 29 2F
Then the first 4 bytes (first column) of the round key for round 9 are calculated as follows:
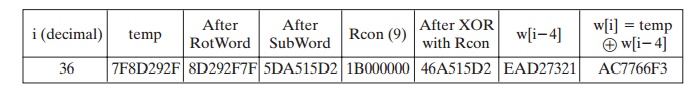
NOTE 5: Round Constant is different for every round. The basic purpose of adding round constant is to add Asymmetry.
















Comments
Post a Comment